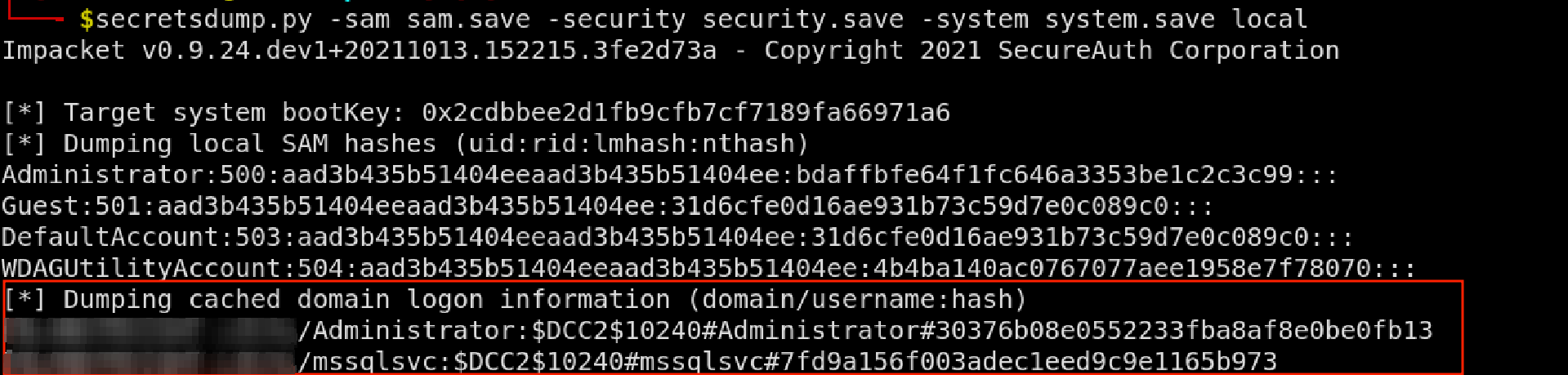
Context: After looking through the a dump of SAM database there was a section called:
Dumping cached domain logon information
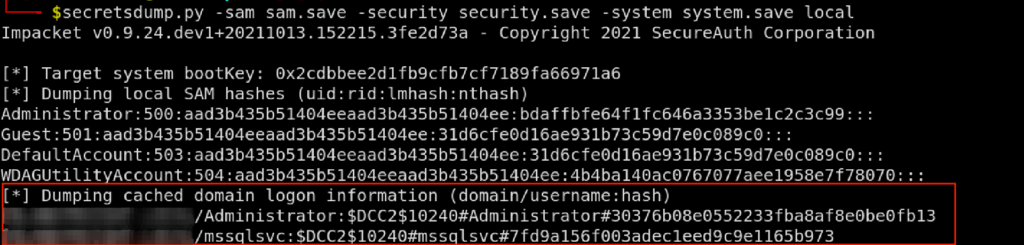
This section listed hashes for 2 domain users, however interestingly I wasn’t able to pass these hashes for a pass the hash attack. After dumping the LSASS process the credentials for the same users were present in the dump but the hash was different, i was able to perform a pass the hash attack with the hash found from the LSASS process.
Now the question that bugged me was: Why was there a false hash in the SAM?
Turns out it wasn’t a false hash. After some documentation reading it seems that Windows has a system in place to cache credentials for the domain users that log into the machine in case the DC is down these credentials can be used to let the user log-in to the system without needing the DC. Source: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/hh994565(v=ws.11)#windows-logon-cached-password-verifiers
However these credentials are not in your usual hash form to mitigate the threat of presenting the credentials to other systems for authentication. The algorithm used for the purpose of caching domain credentials is called MScash Further information about how the settings for the caching can be changed: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/jj852209(v=ws.11)
But it turns out even if you can’t present these hashes for a pass the hash attack, if the hash is of a weak password it can still be cracked as shown in this article: https://www.ired.team/offensive-security/credential-access-and-credential-dumping/dumping-and-cracking-mscash-cached-domain-credentials#cracking-mscash-mscache-with-hashcat
So if you’re on the ends of rope in a pentest this might come in clutch.
Now I wasn’t able to find some program/website from where I could experiment around with generating MScash hashes, however I did learn about the MScash 2 algorithm which has an interesting functionality.
it salts the generated hashes with different pieces of data from the environment of Windows to make the generated hashes resistant against rainbow table attacks with pre-computed hashes. Quite neat, this doesn’t make the hash un-crackable per say, however it does make the process a lot more tedious.
These little nuggets are often very interesting as they lead you down a rabbit hole and you realize how much you don’t know. This was a fun little exercise to try to figure out what was going on under the hood initiated by a simple question of why?